StreamArmor 4.1 Crack & Keygen
StreamArmor is a powerful software solution, capable of scanning your files and disk drives, in order to find malicious or threatening data. It is designed to detect hidden alternate data streams and remove them from your computer, thus protecting you from unwanted processes or files.
The application features integrated scanning tools, for multi threaded ADS search and it can perform an advanced analysis of your system or of selected drives. You can set the software to perform recursive scans of certain files or the entire system and find potentially dangerous file streams.
Download StreamArmor Crack
| Software developer |
SecurityXploded Inc
|
| Grade |
4.6
1170
4.6
|
| Downloads count | 9993 |
| File size | < 1 MB |
| Systems | Windows XP, Windows XP 64 bit, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10, Windows 10 64 bit |
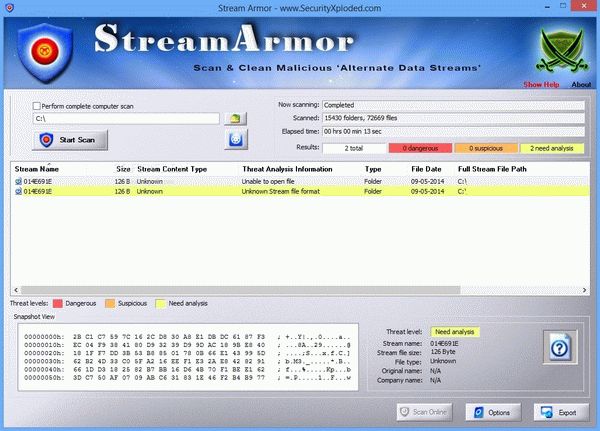
Hidden or unknown streams are displayed along with the level of danger they present. Each hidden stream is rendered on a colored row, from yellow to red, depending on how big a threat they are considered to be.
Thus, red represents dangerous alternate data streams, orange are suspicious streams and those highlighted with yellow require further analysis.
After scanning the selected drive or files, the software can display the identified data streams along with the stream content type, threat analysis information and the complete file path.
If you seek unknown file streams, you may set StreamArmor Serial to ignore the known types and display only the unidentified stream files.
The software offers its own analysis instruments, but also enables you to use online virus detecting services. Moreover, you can use a different application or hex code editor in order to open executable stream files.
Additionally, you may export the results of the analysis to a HTML report. The application also displays a quick snapshot view of the stream layout for your close-up analysis.
StreamArmor is a reliable ADS scanner and cleaner that enables you to detect multiple thread streams that hide suspicious or unknown data. It identifies the threatening files and locates them, so you can take the appropriate action regarding them.
