Legit Log Viewer 1.3.44.30 Crack With Serial Number
Computer operations aren't just pure entertainment. Specialized applications are used to monitor different events, which can be general, or input from connected devices and machines. Most types of info are saved as logs, and it's up to applications like Legit Log Viewer to help analyze and organize them.
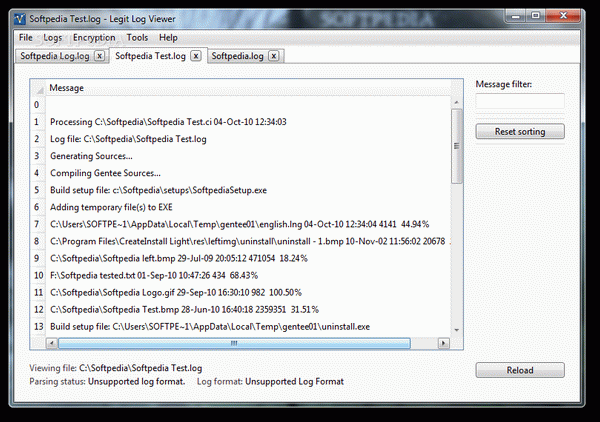
You first need to go through a setup process to ensure the proper deployment of the application. The last step lets you run it directly so you can take it for a spin. The main window shows up, with a demo log file already loaded to quickly check the set of features, filters, and other operations.
Download Legit Log Viewer Crack
| Software developer |
Legit Log
|
| Grade |
3.1
903
3.1
|
| Downloads count | 7029 |
| File size | < 1 MB |
| Systems | Windows XP, Windows XP 64 bit, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 2003 |
On the bright side, you're able to process multiple log files at a time, each stored in its own tab. Supported file formats include LLOG, XLOG, LOG, and TXT, and this is available for both import and export. Additionally, the application offers an encryption algorithm to secure log files. RSA keys are used, with the possibility to create new ones on the spot, export, and import from existing files.
Logs are shown in a neat table, with column headers for process ID, date and time, level, context, logger, and message. Some types can be filtered, while arrangement is easily done by clicking the corresponding header. You can choose which headers to show, and even filter the entire log by message, and highlight particular areas.
Moreover, the application comes with a built-in capture tool to build log files on the spot. Events are usually captured system-wide, but you can edit log formats to choose target components, such as C++ libraries, NLog, DebugView, Windows Installer forms, and more, with the possibility to add your own formats.
All things considered, we can state that Legit Log Viewer Serial is sure to come in handy thanks to its organized approach on log file reading. Logs can be captured in real time from different instances and forms, filtered according to different criteria, exported, and even encrypted for more security.
