Vulnerable URL checker pentest edition 3.0 Crack With Keygen
Vulnerable URL checker pentest edition aims to help website owners and web developers in checking their domain for URLs that might offer cyber criminals a way to infiltrate into the main server. It serves as an additional security tool that can be used in order to find potential security defects.
The application only runs in the command console, but thanks to the straightforward options, you don't have to deal with a complex syntax.
Download Vulnerable URL checker pentest edition Crack
| Software developer |
Dreamwalker Software
|
| Grade |
4.7
823
4.7
|
| Downloads count | 6668 |
| File size | < 1 MB |
| Systems | Windows XP, Windows Vista, Windows 7, Windows 8, Windows 8 64 bit, Windows 10, Windows 10 64 bit |
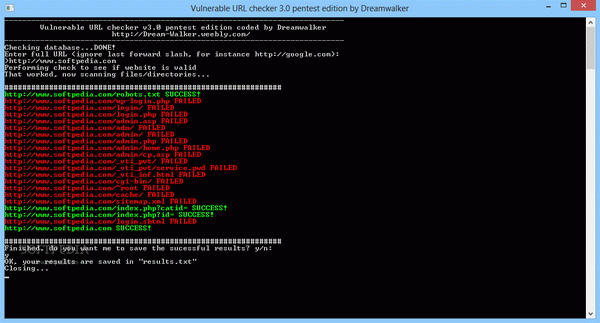
At first launch, the application creates a database of URL extensions (meaning the final part of an URL) to help you get started and then automatically closes. The links are stored in a plain text file, which means that you can extend the list so as to enhance the application's capabilities.
When running it for the second time, the database is checked and you are prompted to enter the URL you want the application to analyze. The program verifies its validity and proceeds to finding potential vulnerabilities.
What it actually does is place the terminations in the database next to the URL of the main domain and check whether the newly formed links are available or not by sending them a ping request and waiting for a response.
Valid links are displayed in green alongside a 'success' message, while non-existent one are shown in red. When the analysis is complete, the successful results can be saved to a text file.
Vulnerable URL checker pentest edition Serial can come in handy to website admins who want to identify security holes.
However, there are various other tools out there that provide a richer feature set, capable of auditing a web server to find potential vulnerabilities such as SQL, LDAP or XPXPATH injections, cross-site scripting, remote file inclusions, buffer overflows and so on. Thus, IT professionals might look for a more comprehensive security tool that can help them safeguard a website against exploits and attack attempts.
