Transposition cipher 3 Keygen Full Version
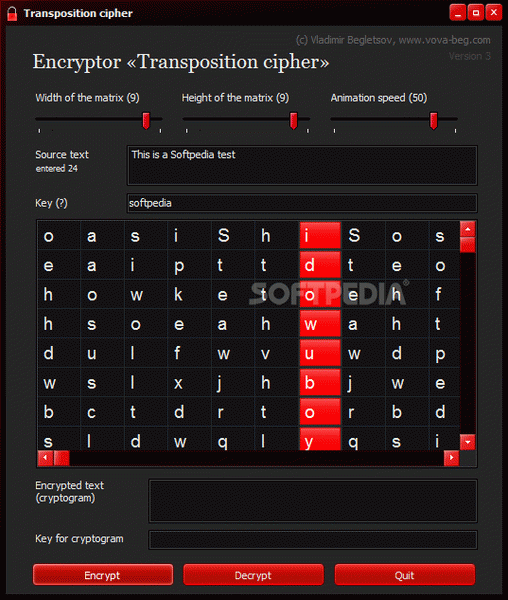
There are many ways to send messages without having to worry about the information falling into the wrong hands, and one of the most common encryption methods is the transposition cipher.
This application uses this algorithm to shift the position of each character according to a regular system. The generated cryptogram can then be decrypted by anyone who knows the exact parameters or has obtained the encryption key.
Download Transposition cipher Crack
| Software developer |
Vladimir Begletsov
|
| Grade |
3.0
787
3.0
|
| Downloads count | 5672 |
| File size | < 1 MB |
| Systems | Windows XP, Windows XP 64 bit, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10 |
While the transposition cipher used by this application may seem rather complex at first, it is actually quite simple, but still very difficult to crack. The utility makes things even easier, however, as you only need to move a couple of sliders or provide an encryption key.
Additionally, you can consult the bundled documentation if you run into any problems, as it provides detailed explanations and helpful screenshots.
Because the application does not need to be installed on your computer, you can launch it from any location and carry it on portable storage devices.
The program enables you to decrypt text obtained from various sources, provided, of course, that you know the matrix dimensions or have the required key.
The resulting message does not contain spaces and may include a few extra characters at the end of the string, but is perfectly readable.
When encrypting or decrypting a message, an animation is displayed that illustrates the whole process. Its speed can be customized, but it is not possible to disable it altogether.
Also, it would be great if the application allowed you to switch to a minimal mode that eliminated the matrix panel to reduce the overall dimensions of the window.
All in all, Transposition cipher Serial is a useful application that makes it possible to encrypt text and decrypt messages secured with this specific algorithm. It is easy to use and offers adequate documentation, in addition to being fully portable.
