Endpoint Protector Basic 13.55.02 Crack Plus Activator
Protecting against malicious attacks is a vital step for any organization or company that wants to secure its assets; even household computers can benefit from these increased security measures. Endpoint Protector Basic allows its users to create basic, but highly effective security rules, effectively denying portable devices full or partial access to the local resources.
The application works with most commonly used endpoint devices and their corresponding ports, such as USB flash drives, memory cards, ZIP drives, digital cameras, Bluetooth units, mobile HDDs, and even smartphones.
Download Endpoint Protector Basic Crack
| Software developer |
CoSoSys
|
| Grade |
4.3
861
4.3
|
| Downloads count | 7303 |
| File size | < 1 MB |
| Systems | Windows XP, Windows XP 64 bit, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10, Windows 10 64 bit |
Employing the application is fairly straightforward, as one must only flag items and the corresponding security rules will be instituted. No advanced knowledge is needed to operate the program, and since this can also be a potential vulnerability, administrators can protect their settings by defining a password check.
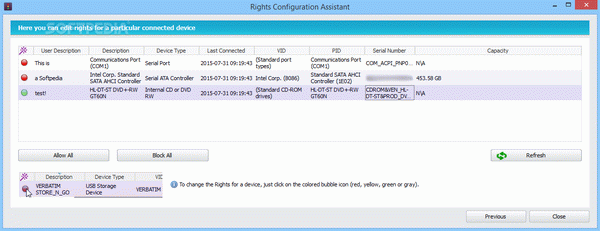
It should also be noted that the application requires Administrative rights to work properly. Once started, the utility automatically displays all the vulnerable ports and devices, complete with VID, PID, serial number, and built-in description values. More-so, one can define customized descriptions for each device, effectively creating security notes or reminders.
As for the protective measures themselves, the tool can institute either full or partial rules; the former means all access is denied while the latter allows read-only access to the computer's resources. Although limited in number, these options give users a certain amount of freedom when configuring their system's protection.
Summing up, Endpoint Protector Basic Serial is a simple, but effective data protection software that will benefit anyone interested in preventing information theft. It can effectively lock down the computer, by preventing access to it from any endpoint devices.
