CrococryptMirror 1.43 Crack With Serial Key Latest
It goes without saying that you do your best to keep your confidential files private, so that nobody can open them without your permission.
CrococryptMirror is one of the apps you can rely on for this purpose, since it encrypts your documents so they cannot be accessed by unauthorized users.
Download CrococryptMirror Crack
| Software developer |
Hissen IT
|
| Grade |
4.9
786
4.9
|
| Downloads count | 6406 |
| File size | < 1 MB |
| Systems | Windows XP, Windows XP 64 bit, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10, Windows 10 64 bit |
After you install the application on your computer and you run it, you need to select the password that will be required whenever you want to explore the encrypted data.
This is why you also get an explanation regarding the type of password that you are recommended to use, so that even applications that specialize in cracking passwords are inefficient. Understandably, you also need to keep the password in a safe place or, better yet, just remember it, otherwise your encrypted files will become off limits.
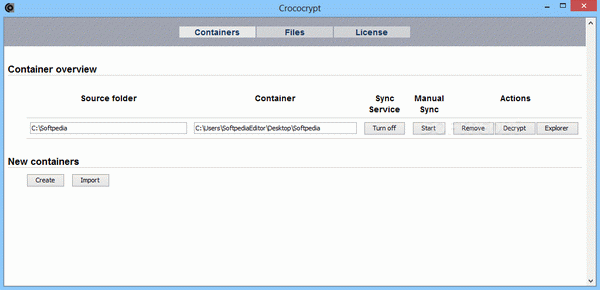
Once you access the main window of CrococryptMirror, you can start creating as many containers as you need, one for each folder where you store your private documents.
You can set the app to automatically mirror the directory’s contents, so that all the files that are added to it also get encrypted. This way, you can sync folders from your PC to your USB drive or a cloud storage folder without worrying that they can be opened by prying users.
The only way to browse the encrypted files is by using CrococryptMirror Serial, so they are safe - if you want to, you can decrypt an entire folder to the location of your choosing or you can decrypt individual files just as easily.
The application uses AES and Twofish encryption algorithms and due to its intuitive GUI, even beginners can benefit from them without too much hassle.
The instructions are clearly presented and explained and users have complete control over the target location of the encrypted container and over the mirroring process (those who do not want it to be used automatically can choose to start it manually whenever they need it).
