Bitdefender Ransomware Recognition Tool 1.0.0.2 Crack + Activation Code (Updated)
Ransomware is nowadays one of the most prevalent forms of cyberattacks, with immense potential criminal profit that turned it into a vicious business model. While more and more attacks happening worldwide, security companies strive to keep up and build reliable decryption tools and antivirus products. Nevertheless, innovation creates new ransomware families and versions so it might be difficult for the regular user to correctly identify the ransomware type that has reached their computer. With that thought in mind, the Bitdefender team created the Bitdefender Ransomware Recognition Tool.
The purpose of this application is to accurately identify the ransomware family and sub-version, then offer suggestions and recommendations of decryption tools that might remove the malware and get the locked data back.
Download Bitdefender Ransomware Recognition Tool Crack
| Software developer |
Bitdefender LLC
|
| Grade |
3.8
790
3.8
|
| Downloads count | 6373 |
| File size | < 1 MB |
| Systems | Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10, Windows 10 64 bit |
In essence, it comes in handy to anyone who suspects they might have been a victim of a ransomware attack, allowing them to find out what kind of decryption tool they should look for.
Delivered in a lightweight package, the Bitdefender Ransomware Recognition Tool Serial does not require installation and, once the user takes note of the license agreement, the main window is shown.
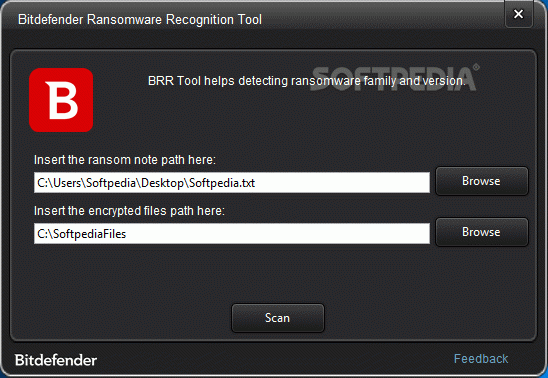
The one-window interface enables you to enter the location of the file that hosts the ransom note (usually a text file on your desktop) and the path of a directory that contains encrypted files. Not both pieces of information are mandatory, but the application requires at least one of them to attempt to identify the type of ransomware the computer is infected with.
Not only that the Bitdefender Ransomware Recognition Tool can detect the ransomware type and version, but it then displays recommendations of decryption tools that might be able to exploit vulnerable encryption algorithms or apply leaked decryption keys to unlock encrypted data. That is, if such a tool exists for that particular ransomware family. Therefore, users have nothing to lose if they try it out.
