MING Network Spy 1.0 Crack + License Key
Using your computer as a main tool for your day to day activities along with an active Internet connection puts your data at risk from various attacks. You or someone else using the same computer might also be the one triggering dangers on your computer by accessing specific web sites, but with applications like MING Network Spy you can keep an eye on network connection data flow.
A connection needs to be set up in order to start monitoring network events. All devices like Ethernet adapters that are used to transfer data are displayed so you can easily select the one you want to keep an eye on. If multiple machines are connected to the same network, you can pick one or more, for increased efficiency.
Download MING Network Spy Crack
| Software developer |
MING Software Inc
|
| Grade |
4.5
1908
4.5
|
| Downloads count | 19426 |
| File size | < 1 MB |
| Systems | Windows 2K, Windows XP, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 2003, Windows 2008, Windows NT |
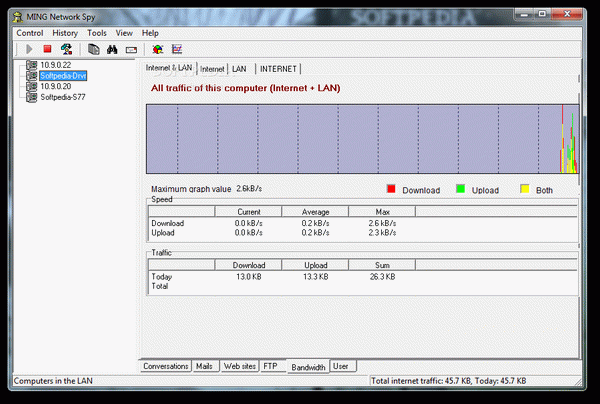
The main window displays a tree view of chosen items. The rest of the space is dedicated to details regarding selected categories. These are stored in tabs, letting you view conversations, mails, web sites, FTP, bandwidth, as well as a general users view.
In order to provide a certain amount of stealth, the application comes equipped with a function that removes the system tray icon, making it possible to bring up the main window only using a custom key combination. This comes in handy if monitoring a single user, with the addition to include a password.
Depending on the type of data and activity you're monitoring, you can set the application to automatically send email notifications to your preferred account with data gathered, either hourly or at midnights. Unfortunately, there's no possibility to export to any kind of file, except having reports printed out on a sheet of paper.
Taking everything into consideration, we can say that Ming Network Spy can be used in order to help prevent potentially harmful attacks or data leaks from servers and important storage devices. Not a lot of effort is required on your behalf, with the possibility to receive log file so you don't constantly check on status.
