Secure Auditor 3.0.20.0024 Activator Full Version
Secure Auditor is a complete security and auditing suite for database servers and Cisco devices, helping administrators efficiently identify vulnerabilities and take the proper actions to reduce risks.
It can perform auditing tasks for SQL server or Oracle database systems, Windows workstations and Cisco routers and switches, trying to detect weaknesses that might be exploited. Its flexibility makes it suitable for networks of all sizes, including those that connect a large number of servers.
Download Secure Auditor Crack
| Software developer |
Secure Bytes
|
| Grade |
4.4
920
4.4
|
| Downloads count | 13192 |
| File size | < 1 MB |
| Systems | Windows 2K, Windows XP, Windows XP 64 bit, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 2003 |
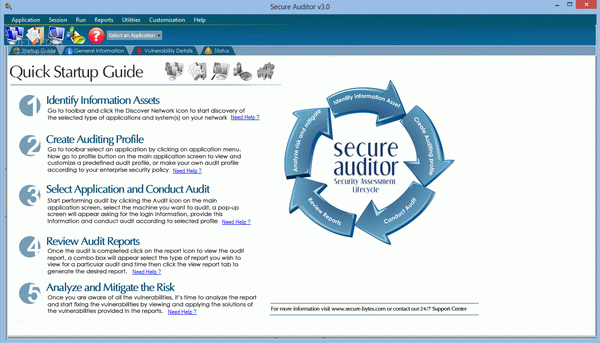
The application welcomes you with a quick startup guide that provides instructions on how to use its functions. You start by scanning and discovering systems in your network (Cisco devices, Oracle or SQL Server instances, Windows workstations) and continue with the selection of a predefined auditing profile. Alternatively, you can create a custom profile that matches the security policy of your company.
Secure Auditor retrieves information about each workstation, including system configuration and technical data, groups and users, shared files and folders, security-related policies (passwords, account permissions and locks), network cards, services, sessions, installed software and identified vulnerabilities.
The gathered data can be comprised in a report with the help of the integrated wizard, which can create both session and audit reports (the latter only includes data related to the detected vulnerabilities and the suggested solutions).
Secure Auditor Serial helps administrators check network devices for all sorts of weaknesses that could compromise its security. Its range of security tools can identify all assets, perform penetration testing and analysis, in the attempt to avoid breaches in the company's network.
From within a single interface, they can control auditing tasks to verify authentication security and discover vulnerabilities and mis-configurations that could create an access point for attackers.
