iStatus 1.0 Build 395 Crack With Keygen Latest
Being in control of the quality of your Internet connection is of critical importance since it can, among others, dictate the nature of your professional relationships, so you cannot afford to experience issues you cannot identify and remedy in real time.
iStatus is one of the software solutions that can be of great help in this regard, given the fact that it can monitor your primary or failover connections and spot any abnormalities.
Download iStatus Crack
| Software developer |
Thinix
|
| Grade |
4.7
756
4.7
|
| Downloads count | 6138 |
| File size | < 1 MB |
| Systems | Windows 7, Windows 8, Windows 10, Windows 10 64 bit |
First of all, you need to know that the program features an approachable GUI, which seems to address users with minimal technical skills as well. The program can hide in the systray in order to reduce its memory footprint, so it is rather improbable to be bothered by it in any way.
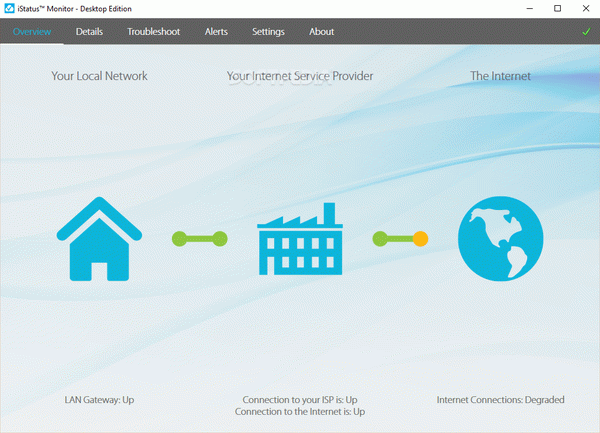
The program’s user interface is split into several categories, namely “Overview,” “Details,” “Troubleshoot,” “Alerts,” and “Settings,” letting you easily check the status of your key connections in no time.
The program allows you to effortlessly identify the root of any network-related problems, letting you actively check the quality of your Internet connection using customizable hosts. Any target can be tested via two different methods, namely ICMP (Ping) and HTTP (Web), with alerts notifying you of any possible issues.
Needless to say, both cellular and wired connections can be monitored, and for security reasons, an ARPWatch component is integrated into the program. What this features can do is ring an alarm if it detects any instance of ARP spoofing that could lead to data leaks via man-in-the-middle, denial-of-service, or session hijacking attacks.
What’s more, setting a PIN code should enhance your security under such circumstances, letting you differentiate between a false and a real alarm.
All in all, iStatus Serial is an intuitive tool that can inform you of any Internet connection failures you may be faced with while also protecting you from unwanted interactions with attackers trying to find cracks in your network.
