Fast Software Audit 1.0.0.0 Crack With Serial Number 2025
Computers in a work environment might only be allowed to run specific programs, either to help employees better focus on tasks at hand, or prevent malicious content from infiltrating. It’s up to the network administrator to keep an eye on things, and one way to do this is through applications like Fast Software Audit.
A neat things about it is that it doesn’t need to be installed on your computer for it to properly run, but you do need to make sure that .NET Framework is a part of Windows. This means you can easily carry it around on a USB flash drive, without worrying that the target PC gets affected in any way.
Download Fast Software Audit Crack
| Software developer |
Chris Wright
|
| Grade |
3.7
922
3.7
|
| Downloads count | 7722 |
| File size | < 1 MB |
| Systems | Windows XP, Windows Vista, Windows 7, Windows 7 64 bit |
Fast Software Audit is meant to be used across a local network, so it’s best to use it on the central computer. What’s more, it needs to be run with administrator privileges to be able to access all sets of data, and LAN computers also need to be under the influence of the main computer.
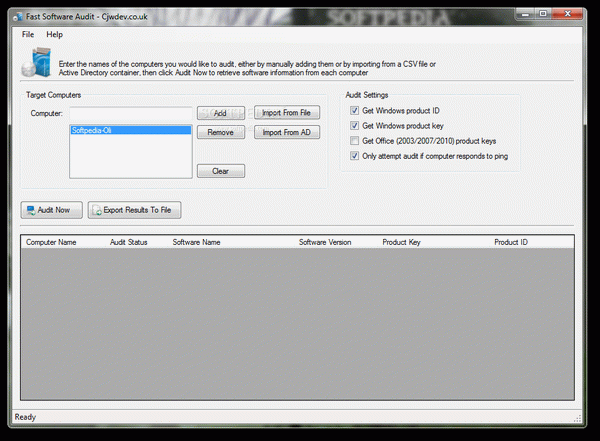
The way in which information is retrieved is by scanning a list of computers you need to create by name. Sadly, the exact PC name needs to be written down, because the application can’t identify a target according to its corresponding IP address. On the other hand, you can import a CSV list with computer names for less effort.
It doesn’t take much for the application to scan, with all info shown in a table with details like computer name, audit status, software name, version, product key, as well as ID. You can choose to audit only if a target responds to ping. There’s the possibility to filter according to column headers, and even export results under the CSV format.
All things considered, we can safely state that Fast Software Audit Serial is a practical application that comes in handy for inspecting computers over a local network to see what applications are installed, and the product key they use to verify authenticity. Sadly, you can’t create the target list by IP addresses, and the table can feel a bit chaotic for too many target PCs.
