Spyware Terminator 2015 3.0.1.112 Crack With License Key Latest
Most computer users protect their workstations using full-fledged antivirus solutions which include or run in conjunction with a firewall. Even if this should provide enough shelter from the ever-spreading malware, an extra layer of security that targets specific threats does not hurt and an application like Spyware Terminator could be just what you need.
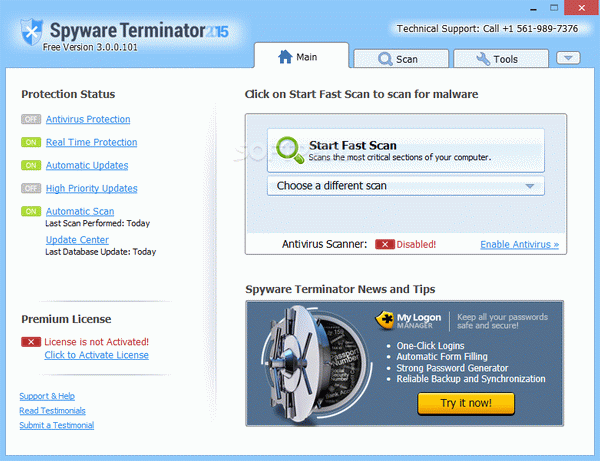
This software has the power to detect and remove spyware and adware. The greatest thing about Spyware Terminator is that it works fast and has all the features you would need to keep malware at bay.
Download Spyware Terminator Crack
| Software developer |
PCRx.com, LLC.
|
| Grade |
4.1
1226
4.1
|
| Downloads count | 132298 |
| File size | < 1 MB |
| Systems | Windows XP, Windows Vista, Windows 7, Windows 8, Windows 10 |
First of all, this utility comes packed with real-time protection, which means the computer is on the safe side all the time, regardless of its Internet connection status. The application monitors the entire activity on the computer and blocks dangerous files from infecting the machine.
Secondly, there is an automatic update option that keeps Spyware Terminator up to date with the latest security definitions, an efficient feature which helps you better protect the PC.
In addition to that, the application provides several scanning modes, on-demand and automatic, one for each type of user. Plus, the on-demand mode includes three different options, fast, full and custom and each of them worked flawlessly during our tests.
The settings menu is pretty rich, and allows you quick access to a lot of options to customize the antivirus, real-time protection or the host-based intrusion prevention system (HIPS). Last but not least, it also comes with a handful of useful tools, such as an online vault, a system optimizer or a startup tuner.
All things considered, Spyware Terminator Serial remains one of the best tools of its kind, and is an easy way to defend your computer against adware, spyware, hijackers, keyloggers and other similar threats.
It does not hinder the system’s performance as the amount of resources used is quite low at all times. Jobs are completed in a timely fashion without popping errors or freezing.
