Monitask 1.6.28 Crack Plus Activation Code
If you own a business and need to check your employees' work without invading their intimacy, by using spy tools without their knowledge and consent, Monitask might help you. This tool not only requires the consent of the employee, but it also gives him a lot of control over the tracking process.
To set up a communication channel between the employer and the employee is very intuitive. The application/client has to be installed on the employee’s computer, while the employer needs only to log in to the online dashboard.
Download Monitask Crack
| Software developer |
Monitask
|
| Grade |
1.0
305
1.0
|
| Downloads count | 1720 |
| File size | < 1 MB |
| Systems | Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10, Windows 10 64 bit |
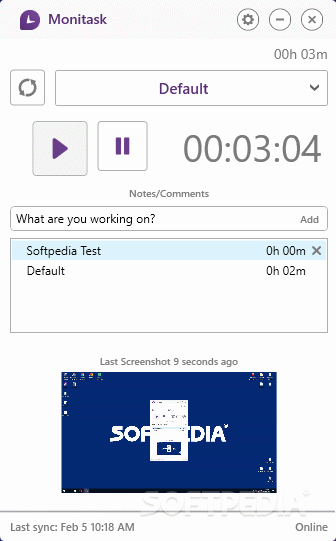
The executable has a compact and simple UI, and all the employee has to do is to start a timer whenever he is working on a project. While the timer is counting, the application will also snap a desktop screenshot, which brings visual proof of the worker’s activity. However, if the Stop Tracking button is hit, no info or screenshots are sent to the online UI.
The Web dashboard is where the employer logs in to receive updates about the team’s progress. Information about the timeline, notes, team members, projects and reports are accessible from there. Furthermore, if you open the Company Settings menu, you get access to a number of tweaks. You can modify both screenshots count and activity tracker, and also set up the idle/offline intervals.
For some users, the screenshot option may sound too drastic but the transparency is not lacking. This can be verified by accessing the client’s settings and looking for the “Notify me when screenshots are taken” entry. If this option is checked, you will always know whenever screen captures are performed.
All in all, Monitask Serial is a simple application that can help companies or private employers to keep track of their team/employee’s work. This app has nothing in common with the intrusive spy tools that invade user privacy, as the outgoing data is mostly controlled by the employee.
