iPhone Eraser 1.0.20 Activation Code Full Version
The personal information that we keep on our phones isn’t as safe as we’d like it to be. This isn’t just about data we provide; all our photos, emails, texts, and browsing cookies can leave traces even after they’ve been “deleted”. In fact, most file recovery programs are based on this.
So, for example, if you decided to sell your iPhone, how can you make sure that the new owner would not be able to easily obtain private information from your device? That’s where applications like iPhone Eraser come in handy.
Download iPhone Eraser Crack
| Software developer |
Apeaksoft Studio
|
| Grade |
4.5
331
4.5
|
| Downloads count | 1819 |
| File size | < 1 MB |
| Systems | Windows XP, Windows XP 64 bit, Windows Vista, Windows Vista 64 bit, Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 10, Windows 10 64 bit |
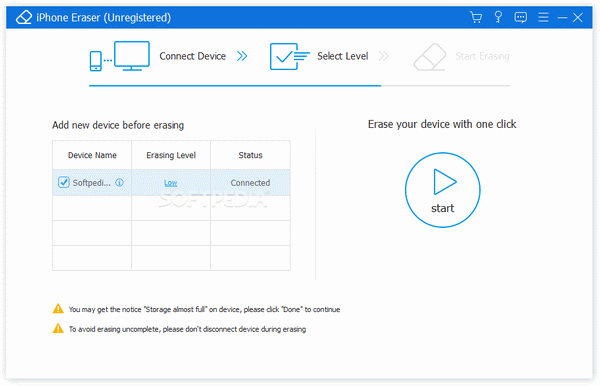
iPhone Eraser isn’t necessarily a software you can appreciate for its versatility. It does what the name says, and nothing more. As soon as you connect an iPhone or iPad to your computer, iPhone Eraser will detect it and ask you how and if you want to proceed.
Now remember that deleting data doesn’t always mean total deletion, so that’s why iPhone Eraser Serial overwrites the information on you device, so it doesn’t leave any traces. Still, if you really want to make sure that you send that private data into oblivion, iPhone Eraser Serial lets you choose between three erasing levels: Low, Medium and High. The last level will overwrite the data a number of three times, thus making your device brand new, just like when it came through that factory door.
If you wish to connect more iOS devices to your computer and format them at the same time, iPhone Eraser allows you to do just that. The program will also automatically generate an activity log, and it can export all of its erasing history as a CSV or PDF file that, well, you can erase later.
Overall, iPhone Eraser is a powerful, even if limited tool, which you can use if you ever become increasingly concerned about security and protection from data theft.
