Privilege Escalation Vulnerability Scan Tool 1.0 Crack + Activation Code Updated
To keep your computer safe from the perils of the web, it's necessary to not only arm it with a powerful anti-malware application but also to resort to additional utilities that can help you spot, fix and prevent security-related problems.
Privilege Escalation Vulnerability Scan Tool is a command-line program specially designed to run a security check on your workstation in order to inspect possible vulnerabilities related to user privileges. These weak spots exist due to some Windows features that can be toggled.
Download Privilege Escalation Vulnerability Scan Tool Crack
| Software developer |
Int64 Software Ltd
|
| Grade |
4.0
676
4.0
|
| Downloads count | 5748 |
| File size | < 1 MB |
| Systems | Windows 7, Windows 7 64 bit, Windows 8, Windows 8 64 bit, Windows 2008 64 bit, Windows 2008 R2, Windows 10, Windows 10 64 bit, Windows Server 2016 |
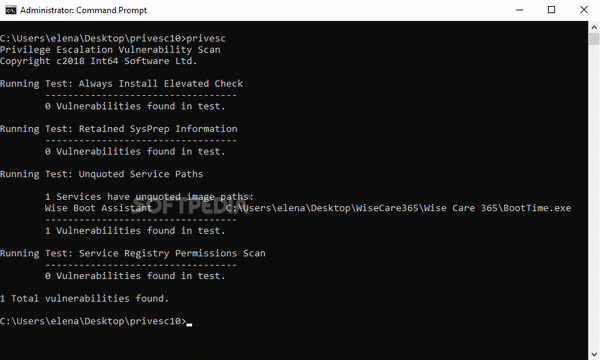
To be more specific, exactly four types of vulnerabilities can be detected by this software utility: "Always Install Elevated", "Legacy SysPrep Configuration Files", "Unquoted Windows Service Paths", and "Windows Service Registry Permissions".
"Always Install Elevated" is a Windows feature that tells the operating system to always install applications or services using system-level privileges by default. This means that the action is not automatically blocked by the computer and then delayed until it's confirmed or denied by the administrator. Leaving this feature active means clearing the way for backdoors, which are likely to take control over your PC.
Sysprep (System Preparation Tool) is a tool used by the OS for clearing security, identification and boot information when preparing the computer for a first-time boot as well as for cloning the OS to be able to install it on multiple workstations within the same network.
Unquoted Windows service paths mean that the full paths to the Windows services are not wrapped in quotes (e.g. C:Program FilesTrustedInstaller.exe instead of "C:WindowsProgram FilesTrustedInstaller.exe"). When this happens and if the full paths contain spaces, the services are prone to exploits.
Lastly, Windows keeps data about how local services are configured within a specific registry entry (HKLMSYSTEMCurrentControlSetServices). However, this information can be altered to change the way the services are executed, so it's necessary to set the configuration correctly, in order to avoid any malware hijacks.
Privilege Escalation Vulnerability Scan Tool Serial checks each of these four vulnerability types and tells you whether or not the tests are successful. Make sure to run it as admin to avoid any permission errors.
Unfortunately, it doesn't have options integrated for resolving the issues, so you have to resort to another application for that, or spend time on the web learning how to do it yourself. On the other hand, you can run scans on other workstations in your local network by specifying the hostname (privesc.exe [hostname]).
Privilege Escalation Vulnerability Vulnerability scanner Scan vulnerability Vulnerability Scanner Scan Checker
