Harden-It 1.2 Crack With Activation Code 2025
Harden-It is a new lightweight software release from YASC .ltd and Zoller Thierry. Harden-it was created to harden your Windows installation against many attacks.
By hardening the IP stack your Network can sustain or completely twarth various sophisticated network attacks. By hardening your Local System lots of current malware, spyware, worm infection are completely blocked, proactively harden your system even against future uknown attacks.
Download Harden-It Crack
| Software developer |
YASC LTD
|
| Grade |
3.0
1802
3.0
|
| Downloads count | 18622 |
| File size | < 1 MB |
| Systems | Windows 2K, Windows XP, Windows 2003 |
Short Features:
■ Harden your server's TCP and IP stack
■ Protect your servers from Denial of Service and other network based attacks
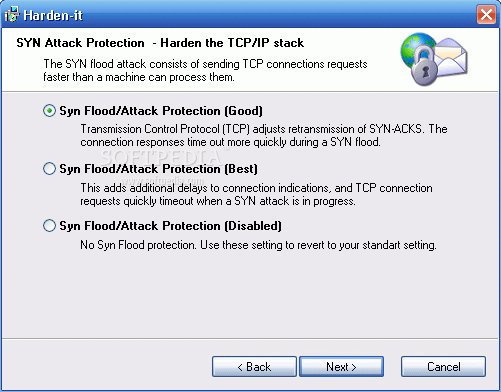
■ Enable SYN flood protection when an attack is detected
■ Set the threshold values that are used to determine what constitutes an attack
Features:
■ Adjusts retransmission of SYN-ACKS. The connection responses time out more quickly during a SYN flood.
■ Determines how many connections the server can maintain in the half-open (SYN-RCVD) state before TCP/IP initiates SYN flooding attack protection.
■ Determines how many connections the server can maintain in the half-open (SYN-RCVD) state even after a connection request has been retransmitted.
■ Specifies the threshold of TCP connection requests that must be exceeded before SYN flood protection is triggered.
■ Controls how many times a SYN-ACK is retransmitted before canceling the attempt when responding to a SYN request.
■ Determines how many times TCP retransmits an unacknowledged data segment on an existing connection. TCP retransmits data segments until they are acknowledged or until this value expires.
■ An attacker could force the MTU to a very small value and overwork the stack by forcing the server to fragment a large number of packets.
■ This setting controls how Windows manages connection keep alive transmissions. Specifies how often TCP attempts to verify that an idle connection is still intact by sending a keep-alive packet.
■ A denial of service (DoS) attack against Windows servers is to send it a "name release" command. This will cause it to release its NetBIOS, preventing clients from accessing the machine
■ Internet Control Message Protocol (ICMP) redirects cause the stack to plumb host routes.
■ Disables ICMP Router Discovery Protocol (IRDP) where an attacker may remotely add default route entries on a remote system.
■ Determines whether TCP performs dead gateway detection. An attacker could force the server to switch gateways, potentially to an unintended one.
■ Specifies AFD.SYS functionality to withstand large numbers of SYN_RCVD connections efficiently.
■ Specifies the minimum number of free connections allowed on a listening endpoint. If the number of free connections drops below this value, a thread is queued to create additional free connections.
■ Specifies the maximum total amount of both free connections plus those in the SYN_RCVD state. Set to lowest for Workstations!
■ Specifies the number of free connections to create when additional connections are necessary.
■ This parameter is used to prevent address sharing (SO_REUSEADDR) between processes so that if a process opens a socket, no other process can steal data from it.
■ NAT is used to screen a network from incoming connections. An attacker can circumvent this screen to determine the network topology using IP source routing. Disables IP source routing.
■ Processing fragmented packets can be expensive. Although it is rare for a denial of service to originate from within the perimeter network, this setting prevents the processing of fragmented packets.Prevents the IP stack from accepting fragmented packets.
■ Multicast packets may be responded to by multiple hosts, resulting in responses that can flood a network. The routing service uses this parameter to control whether or not IP multicasts are forwarded. This parameter is created by the Routing and Remote Access Service.
■ Your computers running Windows may be responding to Address Mask requests on the network, which could enable malicious users to discover some of your network topology information.
■ By default, the DNS resolver accepts responses from the DNS servers that it did not query. This feature speeds performance but can be a security risk.
■ Malicious User Can Shut Down Computer Browser Servic. An vulnerability exists in the computer browser protocol ResetBrowser frame that could allow a malicious user to shut down a computer browser on the same subnet, or shut down all of the computers browsers on the same subnet.
■ Windows NT has a feature where anonymous logon users can list domain user names and enumerate share names.Users who want enhanced security have requested the ability to optionally restrict this functionality.
■ A hidden share is identified by a dollar sign ($) at the end of the share name. Hidden shares are not listed when you look through the shares on a computer or use the net view command. If enabled this option will hide all the administrative shares.
■ Determines how many times TCP sends an Address Request Packet for its own address when the service is installed. This is known as a gratuitous Address Request Packet.
■ Determines the time that must elapse before TCP can release a closed connection and reuse its resources. This interval between closure and release is known as the TIME_WAIT state or 2MSL state.
